Hello again !
Disclaimer: All the material shown on this blog is for educational purposes ! We would not be held responsible for any illegal use of the material by any one !
Usually what happens is that people want to visit a website , which is legit , but some how it is listed in the document given to a naive network administrator and you want to download important stuff from it but what the hell , ITS BLOCKED !!!!!!!! Your boss , teacher or any person whom you report to , doesn’t want hear stuff about BLOCKED SITES !! Its totally lame to them because they want results and you didn’t deliver. This is a very normal problem faced by many employees , students , etc.
First of all you would have to know a little about “Tunnel” . For that please check out my post about Tunneling because your concept of how tunneling works should be very clear. Today I would tell you how one can bypass these filters.
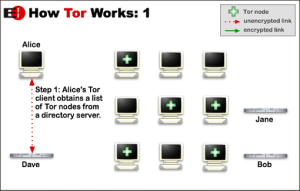
 Tor stands for The Onion Router. This was at first created by the US Naval Research Laboratory a long time ago but then was handed over to the people for commercial use ! Though alot of funding is still coming from the US Govt, and alot of other parties. Which is a pretty good thing because TOR was initially designed for anonymity. The goal was that the users would be anonymous over the internet , thus becoming less of a target for the hackers but back then ” Drive By Malware/Exploits ” were not in mind or yet discovered.
Tor stands for The Onion Router. This was at first created by the US Naval Research Laboratory a long time ago but then was handed over to the people for commercial use ! Though alot of funding is still coming from the US Govt, and alot of other parties. Which is a pretty good thing because TOR was initially designed for anonymity. The goal was that the users would be anonymous over the internet , thus becoming less of a target for the hackers but back then ” Drive By Malware/Exploits ” were not in mind or yet discovered.
In this blog I would cover the bypassing of filters so anonymity is not the main focus.Ok how it works is that first you goto the link and download the Vidalia Bundle . Then once downloaded, install the software and all its components.
After installation run the Vidalia executable. Wait for its icon on the tray of the taskbar, to the right, to become Green. Once that is done , goto the browser’s network option and add following values in the coinciding variables fields :
Proxy Address : 127.0.0.1
Proxy Port : 8118
Ok now save the settings and get out of the options/settings by clicking on OK !
Now your good to go ! To check whether the proxy is working or not goto : What is my IP (dot) com and see your IP Address. For cross checking whether the proxy is working or not , before adding the proxy settings to your browser goto the above mentioned website and note your IP Address and then compare it with the latter!
Enjoy ! If for instance your ISP or Administrator is smart enough to some how block the tor network, goto the TOR control panel and the click the settings button and then goto the netwok tab, it would be something like this :
If you use a proxy to access the internet , usually which is the case in Universities and Offices so this is the option to give proxy to TOR:
There are a few other techniques you could use to bypass the filters , but this one is by far the best.
Peace.
Follow @Xc0resecurity